
As a security partner, Bright Cyber optimises your existing people, processes and technology, as well as future investments. Our focus is on evidence-led security.
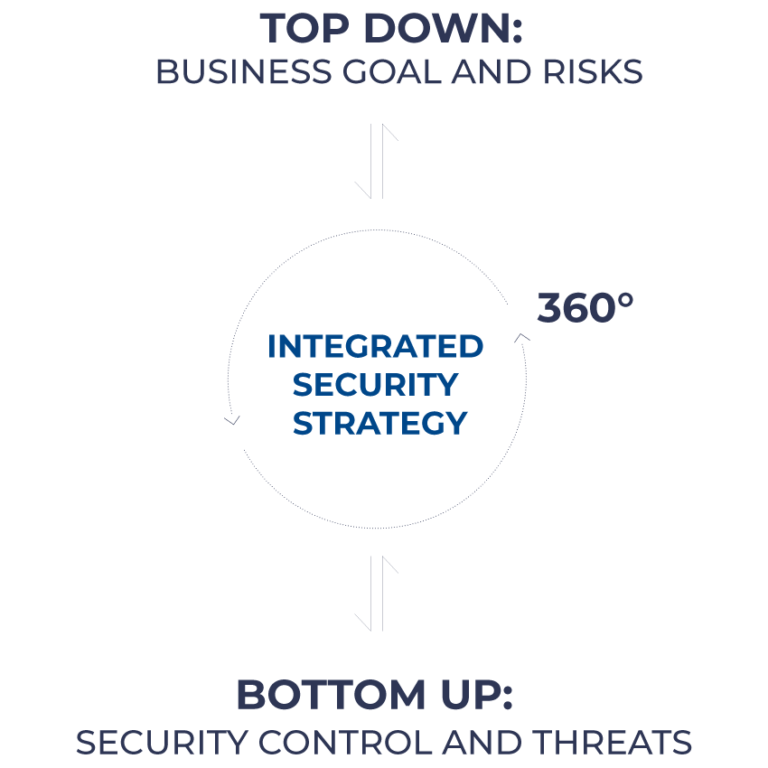
We take a holistic view and improve your security on 3 levels: risk management, security management and security controls.
Move beyond spending more on security, with a better, more sustainable strategy from Bright Cyber.







Support for security leaders and organisations with strategy, consulting and professional services to strengthen their security program.

An integrated risk framework for understanding, communicating and managing exposure and decision-making.





Registered in England as Voodoo Technology Ltd: 7649095 VAT Registration: No. GB 120 1365 72.

To speak to us now, call:
Under Attack? Please call us or click here for free, professional, and immediate Incident Response.
Registered address: 88 Crawford Street, London, England, W1H 2EJ